Discover new heights of productivity and innovation with @Microsoft Surface Copilot+ PC Devices powered by ARM processors. Explore seamless, energy-efficient performance and industry-leading AI. Check out this brochure and contact ContentMX, your authorized Surface partner, to find out more and get your Surface device today!
The Total Economic Impact ™ of Microsoft Dynamics 365 Customer Service
What cost savings and business benefits can you achieve with Dynamics 365 Customer Service? For ideas, read this Forrester TEI survey showing how a composite organization benefitted from a 315% ROI, $1.13 million in new profitability and 40% increase in agent productivity. DM to discuss how Dynamics 365 Customer Service can help your service organization get the actionable insights it needs to accelerate on-boarding and case resolution, improve efficiency, and automate tasks for agents in their flow of work.
Introducing the new Surface Copilot+ PCs
Transform your computing experience with the new @Microsoft Surface Copilot+ PCs. Faster, more powerful, reimagining what’s possible. Watch this eye-opening video demonstrating the amazing things you can do with these devices. Contact ContentMX to get your Surface PC today!
Migrate to Innovate: Be AI-ready, Be Secure
With 90% of companies worldwide making #generativeAI a workforce partner, you need to get your company ready, starting with migrating to the cloud. With @Microsoft Azure, we’ll meet your business where it is in its cloud migration journey. Watch this video and envision the possibilities.
Council Post: AI’s Transformative Impact On Small Businesses
From offloading repetitive tasks to overcoming resource constraints and helping level the playing field with larger competitors, AI’s impact on small businesses cannot be overstated. #businesstransformation
The 7 Revolutionary Cloud Computing Trends That Will Define Business Success In 2025
As we approach 2025, cloud computing continues to evolve, presenting new opportunities for business innovation and efficiency. Bernard Marr’s latest Forbes article delves into seven transformative trends, including the adoption of multi-cloud strategies, the infusion of artificial intelligence, and the growth of edge computing. Gaining insights into these developments is essential for organizations striving to harness the full potential of cloud technology and maintain a competitive edge in the digital era.
Microsoft Copilot for Security
With Microsoft Copilot for Security, defenders are 49% more accurate and 39% faster. Ready. Set GO! Download this whitepaper to see Microsoft Copilot for Security can help you improve the accuracy and speed of cybersecurity activities. #MicrosoftSecurity
(Re)Introducing the Surface Management and Support Suite | Microsoft Community Hub
Explore the newly enhanced Microsoft Surface Management and Support Suite. Streamline @Microsoft Surface device management, simplify warranty, advance sustainability goals, and optimize your budget. ContentMX is your Surface partner with specialized expertise with this solution, so contact us today to get started.
Analytics Lessons Learned: How five companies increased data value with unified analytics solutions
Struggling to extract timely, accurate insights from data? Download this eBook for lessons learned from five companies that rely on Microsoft unified cloud analytics to help them address data problems in a scalable, secure, and timely way.
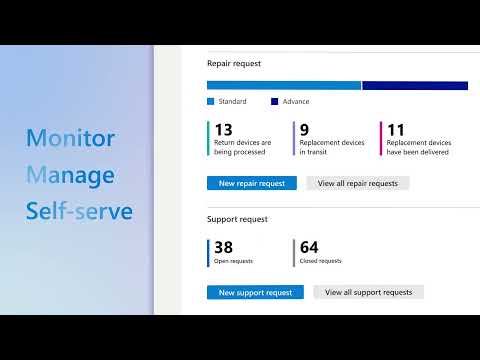
Surface Management Portal
Rethink device management with Microsoft’s Surface Management Portal. Efficiently monitor and manage @Microsoft Surface device at scale. Watch this video to see a demo of this solution and contact ContentMX today to get started.